Sie wurden bekannt, indem sie sorglosen Umgang mit Sicherheit ausnutzten: Mit geleakten E-Mails und gehackten russischen Servern sorgte die Internetaktivisten-Gruppe Anonymous auch jüngst wieder für Schlagzeilen. Doch wer steckt hinter dem Kollektiv? Hier teilen die Investigativ-Journalisten der NZZ ihre Erkenntnisse über Ursprünge, Funktionsweisen und Tätigkeiten von Anonymous mit uns.
Tag Archives: security
“If you don’t use technology consciously, you will be used by it” (40 years of CCC 3)

40 years ago, the Chaos Computer Club was founded in Germany. Steffen Wernéry (middle) was there from the beginning. Today he is no longer active in the front row. He remembers.
You still work in the industry.
Steffen Wernéry: I’m a data protection officer for an operator of anonymised network connections (VPN). I’ve always been less interested in hacking than in hunting for security holes, which others can do better, than in the creative, design side. I first came to computers through my interest in acoustics, photography and video. When I was 20, I did an art project with Bernd Krake in which I transmitted image data by telephone between the Hamburg Kunstverein and the Massachusetts Institute of Technology (MIT).
What about the creative use of technology today?
Steffen Wernéry: Hacking is more necessary than ever. Not in the sense of computer crime, but in the original sense, the critical handling of technology and finding weak points. We are surrounded by unfinished products. Software and hardware have security vulnerabilities, and those who rely on them are quickly finished. Instead of relying on stock and preservation, companies produce technological junk. Even in the literal sense, none of this is environmentally friendly. The products are designed for consumption and to be addictive. People spend less and less time in real life.
Virtual versus real life, I’m surprised that you, as a net activist, see this as a contradiction. Doesn’t one enrich the other?
Steffen Wernéry: Sure, the internet is great if I want to repair my washing machine, if I want to exchange ideas with like-minded people about hobbies or politics, if I want to collect environmental data together with others. But most people sit in a consumption loop, waste their time and think that this is real life. We already said 40 years ago: machines reinforce structures. It happens all by itself. If you don’t use technology consciously, you will be used by it.
Sounds like the CCC has failed.
Steffen Wernéry: The club does what it can. It teaches young people media competence in the project “Chaos macht Schule”. It participates in lawsuits against laws, keeps up the exchange with other institutions. But it is a fight against windmills. That’s why it’s so important to keep some anarchy and fun going. (Questions by Ruth Fulterer)
Starting in 1986, the hackers used a flaw in an operating system to infiltrate other people’s systems and gain access rights there. Computers at the Cern nuclear research centre were among those affected. In 1986, the club newspaper “Datenschleuder” printed an internal complaint about the intruders: “There seems to be a club based in Germany called the ‘chaos club’ whose collective hobby is hacking systems connected to public X25 networks.”
Wernéry and Wau Holland, the club’s leaders at the time, contacted the companies involved and later spoke out to the media when the case became public (above: broadcast from the German TV ARD from 15. September 1987). Then, on his way to a congress where he was to speak about data protection, Wernéry was arrested in France in 1988. He was believed to be an accomplice or even responsible for the hack. The investigators quickly dropped this accusation and he was released. The investigation into his complicity continued for a long time, but in the end came to nothing.
40 years Chaos Computer Club (2)

40 years ago, the Chaos Computer Club was founded in Germany. Steffen Wernéry (on the picture in the middle) was there from the beginning. That’s why he’s already been in prison. Interview.
You soon became the most important figure in the club next to Wau Holland and later wrote the statutes. It says that the club is committed to freedom of information. What does that mean, freedom of information?
Steffen Wernéry: It means the right to freely exchange information. In other words, to communicate in encrypted form, with anyone, about anything, without censorship, without blockades. I find the second part of the statutes particularly important: the CCC is concerned with the effects of technologies on society and individual living beings and promotes knowledge about these developments.
How did you want to achieve all this?
Steffen Wernéry: We organised congresses, meetings and events. We have a magazine, the “Datenschleuder”. Of course, it was also about fun and creativity. What we call in the statutes “promoting the creative-critical use of technology”. We had originally written “hack” in the statutes, but the association register rejected this word because it was not in the Duden dictionary.
It was a hack on the edge of the permissible that made the Chaos Computer Club famous.
Steffen Wernéry: That was in 1984, when the post office had a monopoly on electronic messages. And anyone who wanted to be online had to use a device approved by the post office, which was incredibly expensive. Anyone using untested equipment was liable to a house search and confiscation of the equipment, along with a fine. The user fees for this system, the Internet precursor screen text (BTX), were very high. So the post office, we called them “Gilb”, was the enemy of hate for us. At that time, Wau Holland and I hacked into the BTX access of a Hamburg savings bank and called up a BTX page of the CCC from there, for which we had to pay. By the end of the night, we had booked 135000 D-Mark into our fee account. We made that public. It was embarrassing for the post office, which had claimed that its system was secure. The media jumped on the story. For the first time, data security was a big topic.
What happened next with the CCC?
Steffen Wernéry: That was the beginning of an acceleration. We got new members, there were more and more people on the networks. In 1986, things became more serious. A few people in the club had hacked into Nasa’s computers and sold information to the Soviet secret service KGB. The main participant, Karl Koch, was later found dead. To this day, some say it was suicide, others say it was murder. I myself spent two months in a French prison.
Why?
Steffen Wernéry: At that time, there were hardly any computers on the net. We hackers went where there were networks, for example to the Swiss research centre Cern. That was the European hacker training school. Because there, several people could be on the computers at the same time, chatting online or developing programmes together. Because some of these centres were also used for military purposes, this was quite critical. That’s why there have been investigations since 1986.
How did the trial against you turn out?
Steffen Wernéry: There was never a trial, but the investigations against me lasted 16 years, until 1998, without any result. The Hamburg prosecutor spread the word that I was an East German agent because a picture of Honecker hung in my kitchen. For the French, I was a Nazi because they had found “Mein Kampf” during the same house search. There was also mistrust within the club because of these investigations. It all became too much for me and I quit the front row.
Congratulations: 40 years Chaos Computer Club

40 years ago, the Chaos Computer Club was founded in Germany. Steffen Wernéry was there from the beginning. That’s why he’s already been in prison. Spectacular hacks, even into Nasa’s computers, made the Chaos Computer Club famous in the eighties.
It was seen as a Robin Hood-like hacker gang that is always a little smarter than the powerful and beats them with their own means: the computers . Steffen Wernéry joined shortly after its founding on 12 September 1981 and was at the forefront of the club’s transformation from a nerd regulars’ table to a well-known hacker club.
Today, the club claims to have 8,000 members and hosts one of the world’s largest hacker conventions. The basic philosophy has remained the same: The Chaos Computer Club wants to draw attention to the social consequences of technology and sees hacking as an instrument of enlightenment.
How does your history with the Chaos Computer Club begin?
Steffen Wernéry: It was in 1983 in the left-wing bookshop “Schwarzmarkt” in Hamburg. I had read online that the Chaos Computer Club was meeting there. I hoped to be able to exchange passwords there.
Swap passwords?
Steffen Wernéry: The internet didn’t exist back then, only individual computers on the telephone network. When you found other computers, you wanted to have a look at them. For example, into databases or via the computers of newspapers to the news of agencies in the USA. And the passwords were exchanged with each other.
And did you get any?
Steffen Wernéry: Unfortunately, no. I had to find out that no one from the Chaos Computer Club was online yet. Nevertheless, the visit changed my life. Because I met the founder of the club, Wau Holland. He talked about the computer not only being for the administration and surveillance of citizens. Citizens themselves should use it, for exchange and transparency. He wanted the machine-readable government instead of the machine-readable citizen. That made sense to me. From then on, I was in.
Soziale Netzwerke im Kinderzimmer
Soziale Netzwerke sind schon längst im Kinderzimmer angekommen – immer jüngere Kinder nutzen sie. Influencer auf Plattformen wie Instagram oder YouTube begleiten unsere Kinder im Alltag. Da stellt sich einmal mehr, wie Eltern oder auch ältere Geschwister damit umgehen sollen.
Anlässlich des heutigen Safer Internet Day (SID 2020) fordert Youtuber Robin Blase mehr Medienkompetenz. CAcert erarbeitet zur Zeit entsprechendes Unterrichtsmaterial.
Security is not everything, but without security everything is nothing
 According to estimates, around six million people of the eight million inhabitants in Switzerland use the Whatsapp news service in their private lives. In Germany and Austria, the figures will probably be similarly high. This type of communication is so self-evident that more and more companies want to communicate with their employees and customers with Whatsapp: Picture messages of a place to be repaired, details of a booked flight or even direct advertising.
According to estimates, around six million people of the eight million inhabitants in Switzerland use the Whatsapp news service in their private lives. In Germany and Austria, the figures will probably be similarly high. This type of communication is so self-evident that more and more companies want to communicate with their employees and customers with Whatsapp: Picture messages of a place to be repaired, details of a booked flight or even direct advertising.
The well-known news service explicitly allows operational use and offers a business version for SMEs and an interface (API) for large companies. The list of advantages is long: uncomplicated, direct, shorter decision paths, cost-effective customer service, etc. – what more do you want? Since 2017, however, more and more companies have prohibited their employees from using Whatsapp, as the basic EU data protection regulation stipulates that personal data may neither be collected nor processed without the consent of the person concerned. No company wants to afford the imminent fines of several million euros.
The problem lies in the way the messsanger service operates. It regularly reads the address books of its users in order to compare them with its database. In this way he can display contacts that are new to the service. They have never given their consent. This is therefore a violation of the general data protection regulation, which also applies to companies that have only one contact in the EU. If it is either a service telephone or a private one on which business contacts are stored with the consent of the company, the company is liable. If the employees use their own device in the company, no synchronization with the data processing systems may take place. Thus, the employee processes personal data without the employer’s permission and is then liable for possible violations of the law.
If the intelligence service is to be used in compliance with data protection regulations, there must be two separate address books, one internal, with only those persons who have given their consent to the transfer of their personal data to Whatsapp. Another possibility is the use of a GDPR-compliant messenger in the company. The disadvantage of this solution, however, is that such messengers have not yet become widespread and can therefore hardly be used in contact with customers.
 And the solution? It corresponds to squaring the circle and is about as simple as the browser integration of CAcert in the next 12 months. Nevertheless, it is worthwhile, especially in the year 2019, to deal with how one deals with personal data in one’s company. The first companies to find practicable and easily implementable solutions can gain a competitive advantage, because “Security is not everything, but without security everything is nothing”. (Schopenhauer)
And the solution? It corresponds to squaring the circle and is about as simple as the browser integration of CAcert in the next 12 months. Nevertheless, it is worthwhile, especially in the year 2019, to deal with how one deals with personal data in one’s company. The first companies to find practicable and easily implementable solutions can gain a competitive advantage, because “Security is not everything, but without security everything is nothing”. (Schopenhauer)
The sending of encrypted and signed e-mails is in compliance with the general data protection regulation. With the Organisation Assurance Programme, CAcert offers companies a simple and practical solution. The systematic sending of digitally signed e-mails offers customers the opportunity to clearly distinguish messages from spam and phishing. The encryption of internal e-mails increases security and is technically easy to implement, as the IT department rolls out the corresponding certificates.
Source: NZZ, 31.12.2018
Donate the running costs of allmost one day (5€) Donate as much as you want Donate the running costs of one week (50€) IBAN DE50 2019 0003 0008 5478 07 “CAcert”
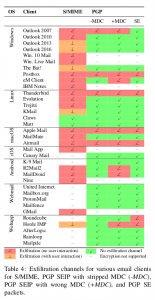
Efail: How you can still trust in GPG/PGP encryption
The EFAIL attacks exploit vulnerabilities in the OpenPGP and S/MIME standards to reveal the plaintext of encrypted emails. In a nutshell, EFAIL abuses active content of HTML emails, for example externally loaded images or styles, to exfiltrate plaintext through requested URLs.
However, according to the German Federal Office for Information Security, the e-mail encryption standards mentioned can be used securely if they are correctly implemented and configured.
There should be no problem, if you and your e-Mail partner use one of the green marked e-mail clients. Even if your client has a red flag, it can be sure; you may do some further research (f.eg. Mailpile). But, do you know the software, others are using? The incident once again demonstrates the importance of trust in communication. Further reading about CAcert’s Web of Trust.
The published vulnerabilities show in particular that, in addition to careful handling of the private key to be kept secret, the security of the e-mail programs used and their configuration can also be decisive.
- Basically, do not display or generate e-mails in HTML format.
- In particular, the execution of active content, i.e. display of e-mails in HTML format and reloading of external content, should be switched off.
- If an e-mail provider offers the possibility to do this via the settings of its webmail application, appropriate measures should also be implemented here.
- Some vendors will publish patches that either fix the EFAIL vulnerabilities or make them much harder to exploit. So, update your e-mail client and the encryption extension.
For sensitive information that must be sent by e-mail, the following procedure can be used: Decrypt S/MIME or PGP emails in a separate application outside of your email client. Decrypt incoming encrypted emails by copy&pasting the ciphertext into a separate application that does the decryption for you. That way, the email clients cannot open exfiltration channels. This is currently the safest option with the downside that the process gets more involved.
Webmail seams not to be under attack, neither Mailvelope or PEP. All of them are not affected. So, the conclusion should not be to uninstall encryption, but to review your e-mail client, update it and adjust the properties.
CAcert.org is a community-driven Certificate Authority that issues certificates to the public at large for free. These certificates can be used to digitally sign and encrypt email, authenticate and authorize users connecting to websites and secure data transmission over the internet. CAcert has more than 358 000 users, is operated by volunteers and financed by donations.
Further reading:
OpenPGP is safer than S/MIME (by GnuPG)
ATE Nykobing, Denmark on September 20th 2015
[Danish and German version below]
On Sunday 20th September there will be “A day of Internet Security and CAcert ATE” hosted by ShowIT Media [1].
Agenda
10:00 Welcome
10:15 A Security status on the Internet by Bitdefender
11:00 A Quick Introduction to CAcert
11:20 Time out for lunch
12:15 CAcert Assurance Training Event (ATE)
17:00 Thank you for coming / Safe journey home.
All speeches will be held in English. There will be the possiblity to gether at least 100 Assurance Points.
Place:
ShowIT Media
Slotsbryggen 14 A-D
4800 Nykobing F
Denmark
More information can be found [2], to register: I will attend the ATE Nykobing
[1] https://www.showitmedia.eu/uk_cert.html
[2] https://wiki.cacert.org/Events/2015-09-20-ATE-DK-Nykobing
[Danish version]
Søndag den 20. September afholdes ”En dag med Internet sikkerhed og CAcert ATE” hos ShowIT Media [1].
Program:
10:00 Velkomst
10:15 ”En status på sikkerheden på internettet” af Bitdefender
11:00 En kort præsentation af CAcert
11:20 Frokostpause
12:15 CAcert Assurance Training Event (ATE)
17:00 Tak for I dag / Kom godt hjem
Alle indlæg holdes på Engelsk. Det vil være muligt at samle mindst 100 Assurance point.
Du kan finde mere information på [2] og registrere dig her: Jeg deltager i ATE i Nykøbing
[German version]
Am Sonntag den 20. September veranstaltet die ShowIT Media “Einen Tag der Internetsicherheit und ein CAcert ATE/”A day of Internet Security and CAcert ATE” [1].
Agenda
10:00 Grußwort
10:15 Ein Sicherheitsstatusbericht für das Internet durch Bitdefender
11:00 Eine kurze Dartstellung von CAcert
11:20 Mittagspause
12:15 CAcert Assurance Training Event (ATE)
17:00 Ende der Veranstaltung
Alle Vorträge werden in Englisch gehalten. Es wird die Möglichkeit bestehen mindestens 100 Assurancepunkte zu sammeln.
Weitere Informationen zum Event unter [2], zum Anmelden: Ich nehme ATE in Nykobing teil.
Disabling SSL3 and 3DES support to improve security for CAcert’s users
CAcert intends to disable SSL3 and 3DES support for its main website www.cacert.org by December 1, 2014.
The main CAcert website is currently still supporting the SSL3 protocol for secure connections. However, in https://www.openssl.org/~bodo/ssl-poodle.pdf it is shown that SSL3 is susceptible to certain cryptograhical attacks. While www.cacert.org does support the recommended TLS_FALLBACK_SCSV option to protect clients with that same protocol option against unintended downgrades to SSL3, this still leaves plain old SSL3 clients vulnerable for the new attack.
Similarly, www.cacert.org is currently still supporting the 3DES cipher suite for encyrpting secure connections. However, this provides only 112 bits of security, which is below the currently recommended number of 128. Hence we should disable it to protect CAcert’s clients.
In practice, the only client known to negotiate SSL3 with www.cacert.org is Internet Explorer 6.0 as found in Windows XP. Thus disabling SSL3 will block https access for these clients only. Similarly, 3DES will only be negotiated by IE 6 and IE 8 running on Windows XP. Since Windows XP is no longer supported by its vendor, and the widely circulated advice to all its users is to switch to a more recent operating system (or switch at least to a more current browser), announcing termination of support for SSL3 and 3DES by CAcert on December 1, 2014 does not seem unreasonable, and is fully in line with our mission to support the security of its users.
If you want to discuss this issue further, please use the bug tracker created for this issue (https://bugs.cacert.org/view.php?id=1314).