The EFAIL attacks exploit vulnerabilities in the OpenPGP and S/MIME standards to reveal the plaintext of encrypted emails. In a nutshell, EFAIL abuses active content of HTML emails, for example externally loaded images or styles, to exfiltrate plaintext through requested URLs.
However, according to the German Federal Office for Information Security, the e-mail encryption standards mentioned can be used securely if they are correctly implemented and configured.
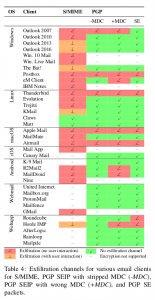
There should be no problem, if you and your e-Mail partner use one of the green marked e-mail clients. Even if your client has a red flag, it can be sure; you may do some further research (f.eg. Mailpile). But, do you know the software, others are using? The incident once again demonstrates the importance of trust in communication. Further reading about CAcert’s Web of Trust.
The published vulnerabilities show in particular that, in addition to careful handling of the private key to be kept secret, the security of the e-mail programs used and their configuration can also be decisive.
- Basically, do not display or generate e-mails in HTML format.
- In particular, the execution of active content, i.e. display of e-mails in HTML format and reloading of external content, should be switched off.
- If an e-mail provider offers the possibility to do this via the settings of its webmail application, appropriate measures should also be implemented here.
- Some vendors will publish patches that either fix the EFAIL vulnerabilities or make them much harder to exploit. So, update your e-mail client and the encryption extension.
For sensitive information that must be sent by e-mail, the following procedure can be used: Decrypt S/MIME or PGP emails in a separate application outside of your email client. Decrypt incoming encrypted emails by copy&pasting the ciphertext into a separate application that does the decryption for you. That way, the email clients cannot open exfiltration channels. This is currently the safest option with the downside that the process gets more involved.
Webmail seams not to be under attack, neither Mailvelope or PEP. All of them are not affected. So, the conclusion should not be to uninstall encryption, but to review your e-mail client, update it and adjust the properties.
CAcert.org is a community-driven Certificate Authority that issues certificates to the public at large for free. These certificates can be used to digitally sign and encrypt email, authenticate and authorize users connecting to websites and secure data transmission over the internet. CAcert has more than 358 000 users, is operated by volunteers and financed by donations.
Further reading:
OpenPGP is safer than S/MIME (by GnuPG)