This weekend, the Security Policy goes into DRAFT. We’ve battled and we’ve won: consensus has erupted in policy group. Not only do we get our Security Policy, but SP going to DRAFT marks a major milestone for CAcert:
We now have a complete set of policies for audit !
We’ve been close before, but never the cigar. In early 2009, some audit work was done, but with gaps: the CPS and the “index” were missing. The CPS came into DRAFT in June 2009, it was close enough at the time. The “index” is called the Configuration-Control Specification (CCS), which is a rather clumsy name for such a simple thing. CCS is a list to all the assets that have to be audited, so it’s worth a little attention. The structure more or less looks like this:
Audit => Criteria (we call them DRC) => CCS (the index)
Then, with CCS in hand, the Auditor can find the parts needed:
--> Policies
/
CCS ==----> critical systems
\
--> roles in control, etc
CCS was the missing link. Luckily the index CCS is relatively easy to write, if all the other policies and systems are clear, and this also means it was doomed to always be last, once the other policies were clear. A month back policy group pushed it through, we brought the CCS finally into its place as a (DRAFT) binding policy.
Which should have been the completion of our policy set for audit, but as CCS was finishing, the Board of CAcert Inc decided to veto the Security Policy, as they can under the rules (PoP 4.6). Now, much has been written about this drama in the maillists, and the debate did raise some serious questions at the time, but they can be left for another day. This week, then we in policy group are taking Security Policy back to DRAFT. Has anything changed? Here are the major points of change:
- The part about the Board Members having a background check has been removed. This was reasonable, as, on the whole, the ABC process is too clumsy for the Board, and the Board now has its own requirements to deal with conflicts of interest, courtesy of the new Associations Act 2009.
- Application Engineer is removed, and that capability is returned to the Systems Adminstration team leader. T/L can bring in a Software Assessor any time he needs one, and take on that risk, etc.
- One non-difference is that SP was still binding on the critical roles, because they accept the SP as their binding document when they are appointed. This is part of the process, as documented in Security Manual. The reason for this is that, under the principles of data protection, anyone who can access the data needs a special agreement, and in CAcert, the SP is that agreement.
- Meanwhile, SP goes back to being binding on the Community. Why would the Community need to be bound to Security Policy, when they can’t do anything wrong anyway? Well, because there are always errors, holes, bugs, omissions and short cuts. In any process! So, while we should fix these omissions, it helps to have the big stick of policy to wield as well. Just because you find a software bug doesn’t mean you can exploit it, and just because you have a title like “auditor” doesn’t mean you can stare at the private root key. We all have wider obligations, and SP is one of them.
Other than tighter wording, etc, that’s it. Welcome to our complete Policy set!
Which final comment brings us to the success of CAcert’s Policy project. It was 5 calendar years in the making, starting off with Christian’s original CPS, and it cost many Member-Years of effort. Some examples: The SP was probably a Member-Year of effort. The CPS is likely equal, the agreements and foundations (CCA, DRP, PoP, etc) another huge lump. I said CCS was an easy one to write, but “easy” still runs to around a Member-Month of effort. PoJAM, similar.
If we think how much a commercial company pays for a Member-Year of effort (100k, plus or minus), that’s a serious investment.
Thank your policy group, and help out with reading and voting!
35 decisions, 13 policies to DRAFT and beyond, 55 contributors. Here’s the top ten, a Hall of Fame, collected a wiki-scraping script I wrote last night:
| Name |
# |
Decisions |
| Tomáš |
10 |
p20100510,p20100426,p20100401,p20100119,p20100113,p20091108,p20091106,p20090706,p20090327,p20081016 |
| Faramir |
10 |
p20100510,p20100426,p20100401,p20100326,p20100120,p20100119,p20100113,p20091106,p20090706,p20090327 |
| Lambert |
10 |
p20100426,p20100401,p20100326,p20100113,p20091108,p20091106,p20090706,p20090327,p20090105.1,p20081016 |
| Philipp D |
9 |
p20100510,p20100426,p20100401,p20100113,p20091106,p20090706,p20090327,p20090105.1,p20081016 |
| Pieter |
8 |
p20100510,p20100426,p20100401,p20100306,p20100120,p20100113,p20091106,p20090327 |
| Iang |
8 |
p20100510,p20100426,p20100306,p20100120,p20100119,p20100113,p20091106,p20090706 |
| Ulrich |
7 |
p20100510,p20100426,p20100401,p20100326,p20100306,p20100120,p20100119 |
| Ted |
7 |
p20100510,p20100120,p20100119,p20100113,p20091106,p20090706,p20081016 |
| Brian |
7 |
p20100510,p20100426,p20100401,p20100119,p20091108,p20091106,p20090706 |
| Morten |
6 |
p20100510,p20100426,p20100306,p20100120,p20100119,p20100113 |
(That’s not a formal result, and it only counts voters from the last 2 years, many others did other things that are harder to measure.)
We now have a set of policies that not only deals with the criteria of the Audit (DRC), not only removes that critical path blockage of documentation for audit, but also presents the only honest, fair, presentable and sustainable policy set in the entire business. In my humble opinion.
This is a set of documents everyone can be proud of. On this foundation we can build. We can, for our Members, create business of real value, not just issue certificates that defy valuation to people who don’t understand their need.
Now, on to implementation and audit. Questions about the audit are questions about implementation, so don’t forget:
Do not ask when your audit is done, rather, ask how you, yourself, are doing your audit!
And now, you’ve got the full policy set, so you know what the Auditor is going to be looking for 😉




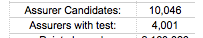


 Verifying the Assurers across the planet is a challenge we must conquer, because our audit criteria says “A.2.y The CP details how the CA verifies that [Assurers] operate in accord with the CA’s policies.” Indeed, the auditor for a big famous-name CA simply declined to audit their web of trust, and the CA found it in its heart to drop the entire thing.
Verifying the Assurers across the planet is a challenge we must conquer, because our audit criteria says “A.2.y The CP details how the CA verifies that [Assurers] operate in accord with the CA’s policies.” Indeed, the auditor for a big famous-name CA simply declined to audit their web of trust, and the CA found it in its heart to drop the entire thing.


